The attacker left a file with a ransom demand, which points to a site where they’re demanding payment to release the victim’s files.
We suspect that the attacker may not have been acting entirely on their own. There may be a connection between the attacker and a larger ransomware-as-a-service ring.
Analyze the demand site, and see if you can find a connection to another ransomware-related site.
Downloads:
Prompt:
- Enter the domain name of the associated site.
In my opinion, this was the easiest task.
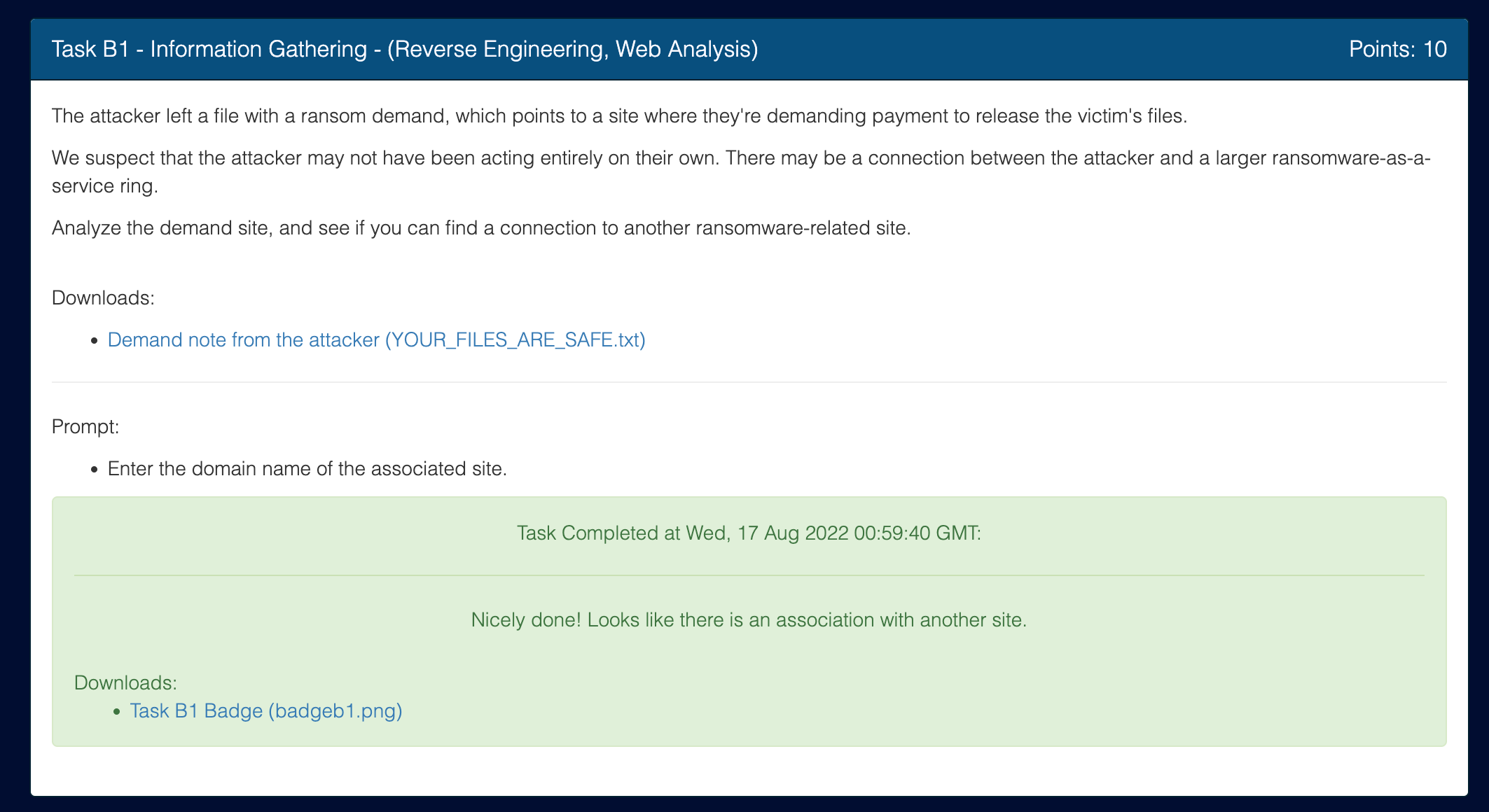
Let’s start by opening the ransom note from the attacker in Google Chrome.
Your system has been breached by professional hackers. Your files have been encrypted, but they are safe.
Visit https://ivjeamomhubeuwen.unlockmyfiles.biz/ to find out how to recover them.
When we visit the site, we find a countdown timer with instructions for payment.
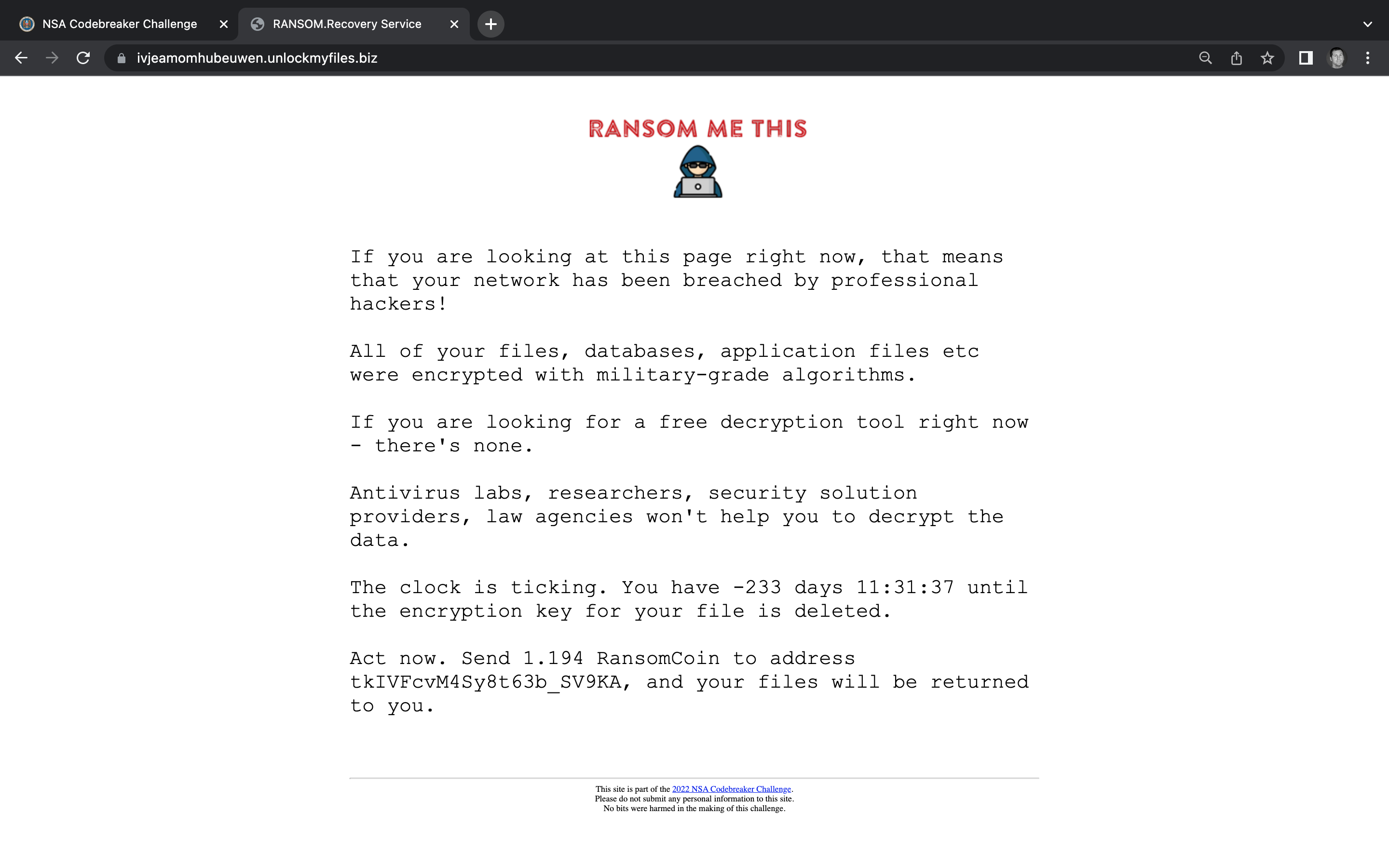
Whenever there seem to be dynamic attributes on an HTML page, you should always inspect the contents. By right clicking anywhere in the webpage and clicking Inspect, you can open the Developer Tools. If we click on the Sources tab in the Developer Tools, we can see a list of all the files used to populate the website.
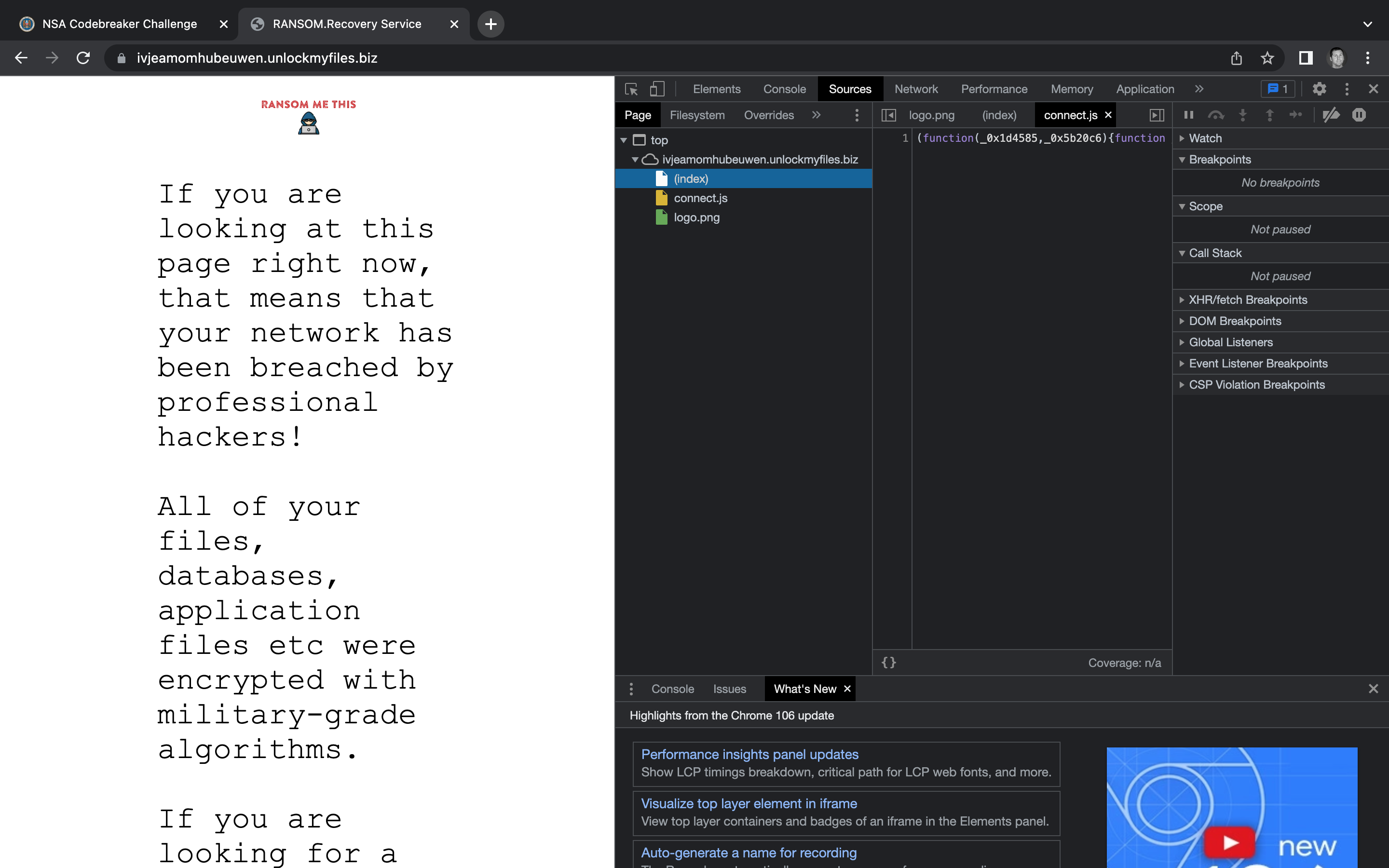
Looks like there are three files:
index.htmlconnect.jslogo.pngLet’s see if there are any other sources for content by visiting the Network tab and refreshing the page.
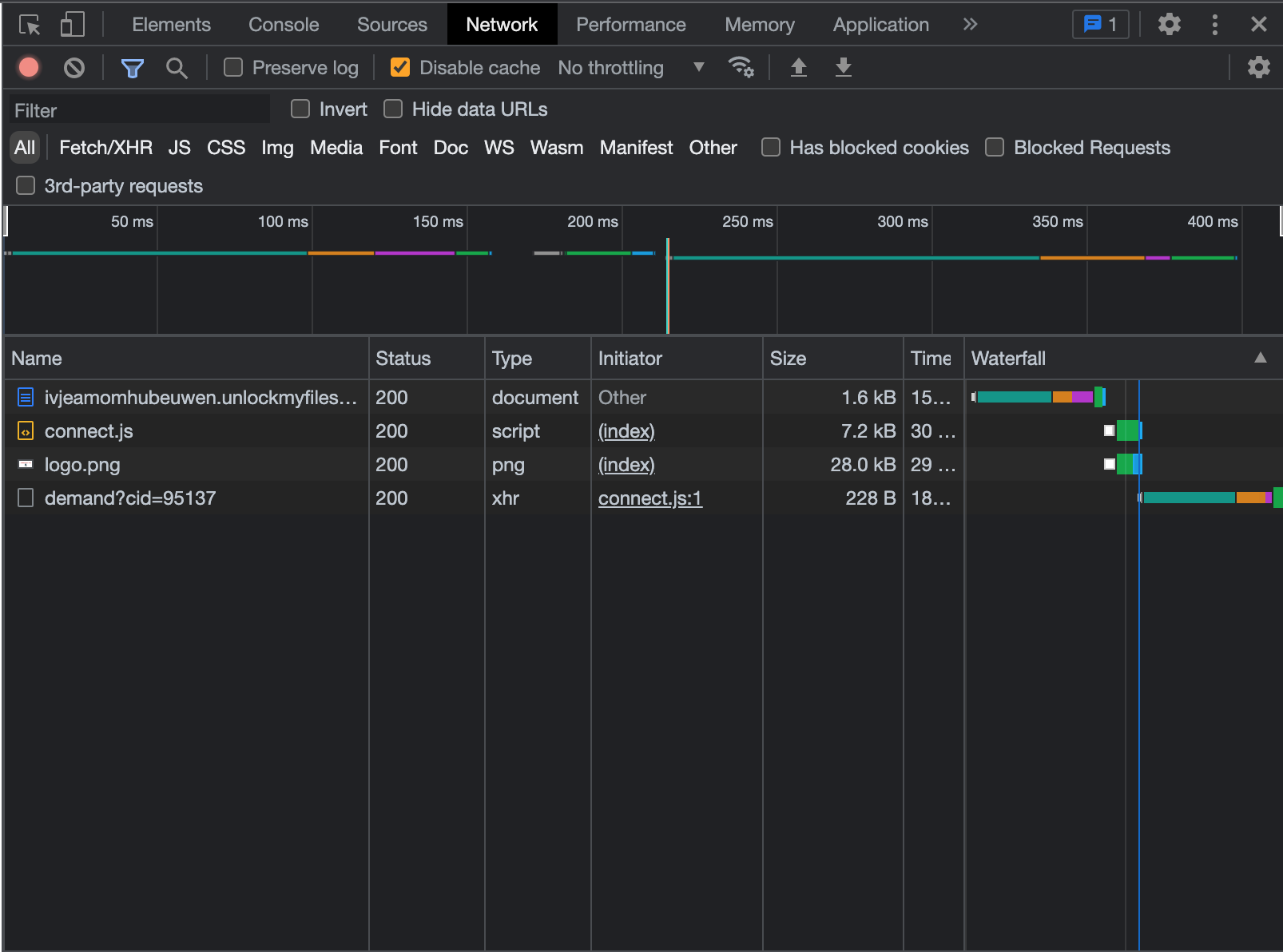
After the reload, we can see that another source, demand?cid=95137, has appeared after it was called by connect.js. Let’s select the source to view the origin.
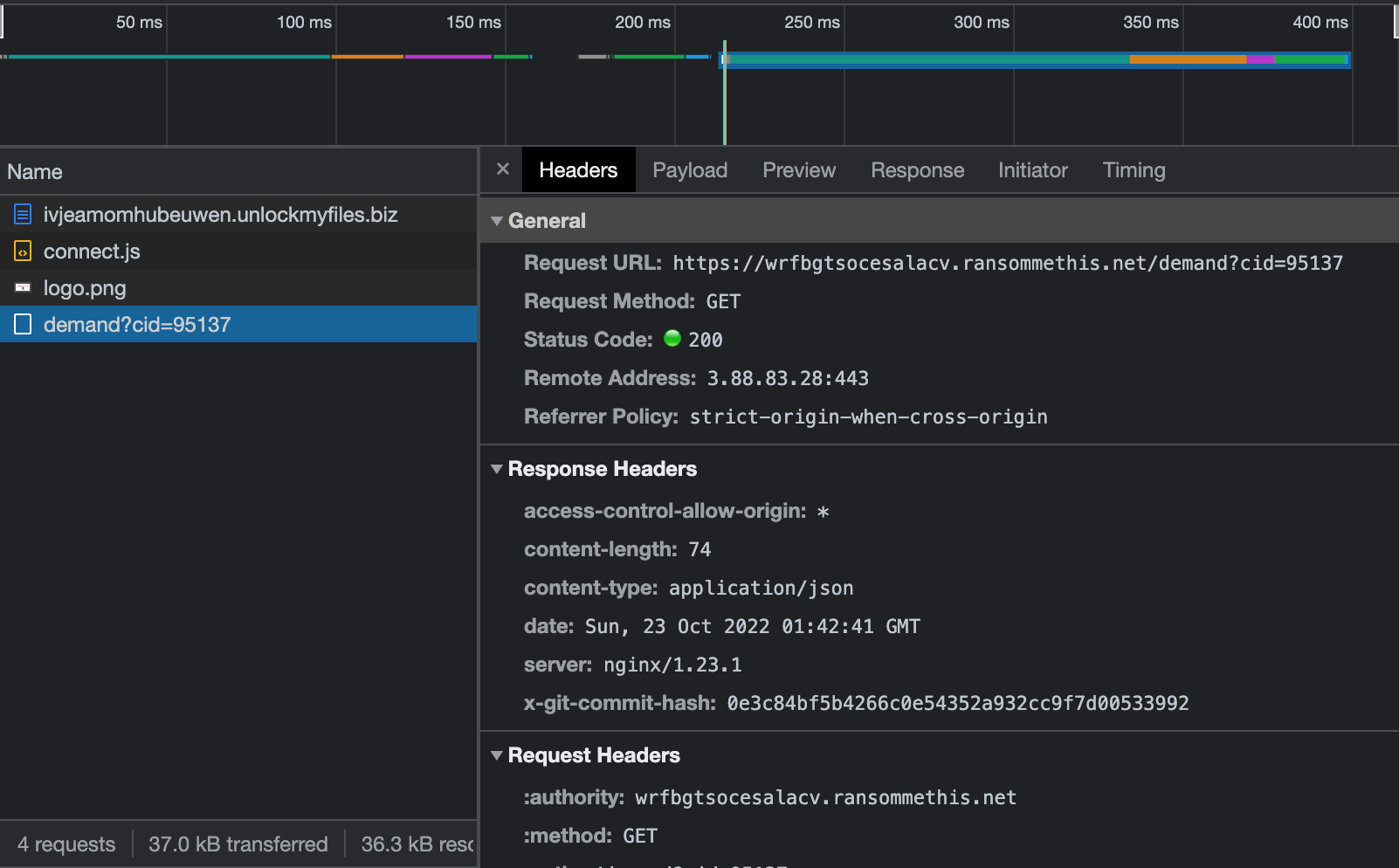
Looks like the request queried a page at the URL https://wrfbgtsocesalacv.ransommethis.net/. When we enter that value into the NSA Codebreaker site, we get a green banner. Success!!!